Question 126
A cybersecurity analyst is currently checking a newly deployed server that has an access control list applied. When conducting the scan, the analyst received the following code snippet of results: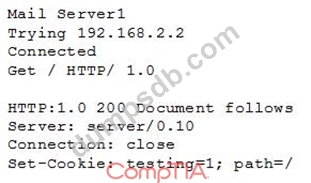
Which of the following describes the output of this scan?
Question 127
An organization has been conducting penetration testing to identify possible network vulnerabilities. One of the security policies states that web servers and database servers must not be co-located on the same server unless one of them runs on a non-standard. The penetration tester has received the following outputs from the latest set of scans: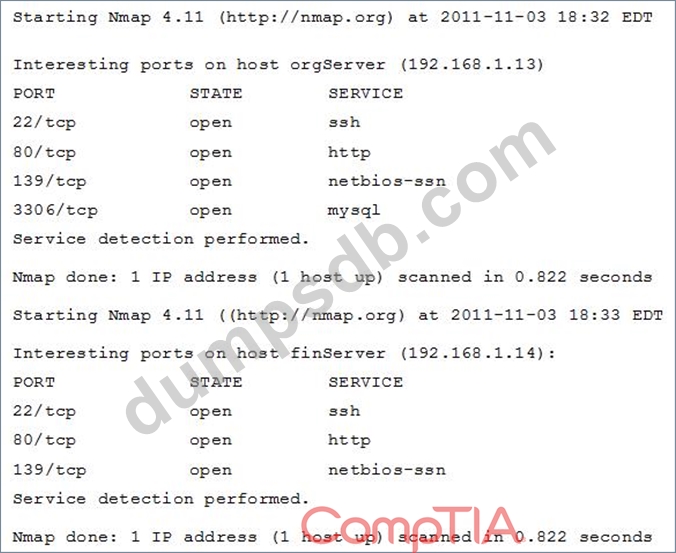
Which of the following servers is out of compliance?
Question 128
An organization is conducting penetration testing to identify possible network vulnerabilities. The penetration tester has received the following output from the latest scan: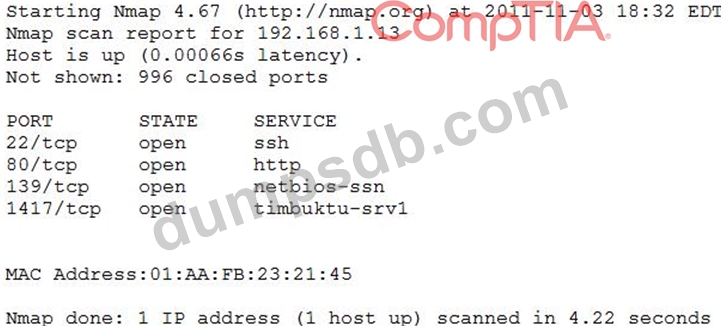
The penetration tester knows the organization does not use Timbuktu servers and wants to have Nmap interrogate the ports on the target in more detail. Which of the following commands should the penetration tester use NEXT?
Question 129
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
Question 130
A security audit revealed that port 389 has been used instead of 636 when connecting to
LDAP for the authentication of users. The remediation recommended by the audit was to switch the port to 636 wherever technically possible. Which of the following is the BEST response?

