Question 136
During a review of security controls, an analyst was able to connect to an external, unsecured FTP server from a workstation. The analyst was troubleshooting and reviewed the ACLs of the segment firewall the workstation is connected to: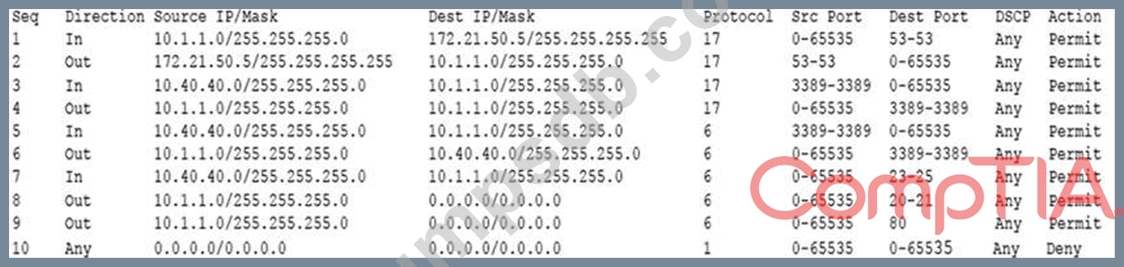
Based on the ACLs above, which of the following explains why the analyst was able to connect to the FTP server?
Question 137
A security analyst has determined the security team should take action based on the following log:
Which of the following should be used to improve the security posture of the system?
Question 138
A cybersecurity analyst is reviewing the following outputs: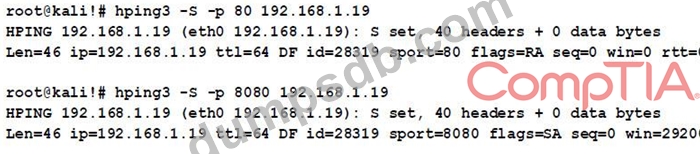
Which of the following can the analyst infer from the above output?
Question 139
An organization wants to remediate vulnerabilities associated with its web servers. An initial vulnerability scan has been performed, and analysts are reviewing the results. Before starting any remediation, the analysts want to remove false positives to avoid spending time on issues that are not actual vulnerabilities. Which of the following would be an indicator of a likely false positive?
Question 140
An organization recently had its strategy posted to a social media website. The document posted to the website is an exact copy of a document stored on only one server in the organization. A security analyst sees the following output from a command-line entry on the server suspected of the problem:
Which of the following would be the BEST course of action?

