Question 131
An organization recently had its strategy posted to a social media website. The document posted to the website is an exact copy of a document stored on only one server in the organization. A security analyst sees the following output from a command-line entry on the server suspected of the problem:
Which of the following would be the BEST course of action?
Question 132
HOTSPOT
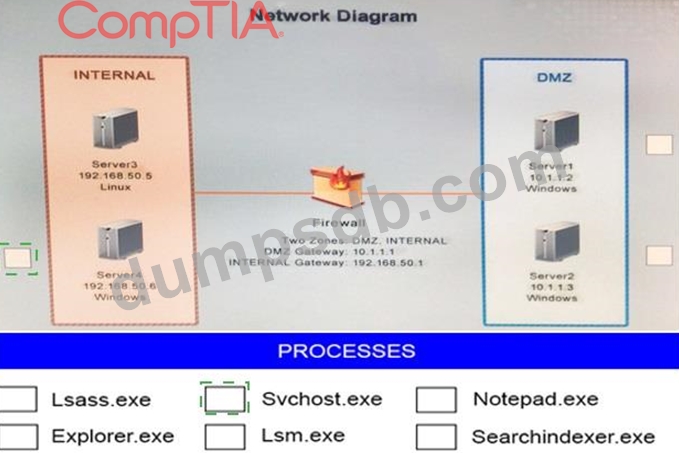
Malware is suspected on a server in the environment. The analyst is provided with the output of commands from servers in the environment and needs to review all output files in order to determine which process running on one of the servers may be malware. Servers
1, 2 and 4 are clickable. Select the Server which hosts the malware, and select the process which hosts this malware.
Instructions:
If any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.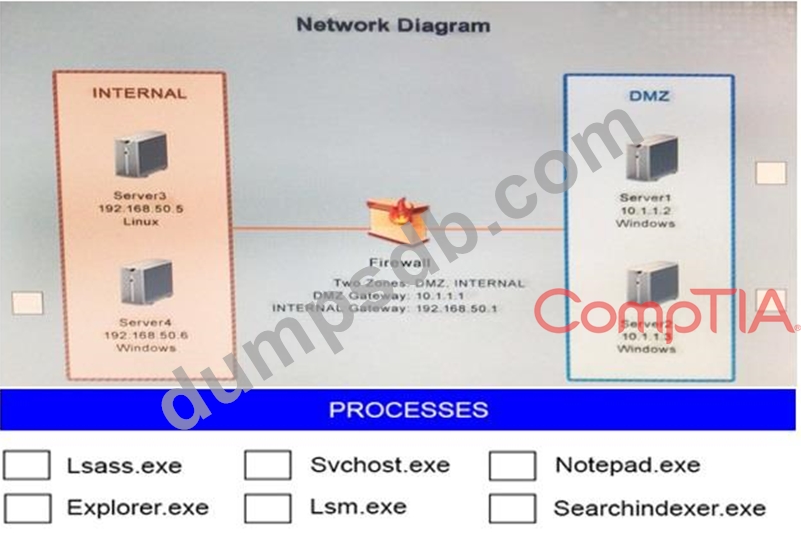
Question 133
After a recent security breach, it was discovered that a developer had promoted code that had been written
to the production environment as a hotfix to resolve a user navigation issue that was causing issues for
several customers. The code had inadvertently granted administrative privileges to all users, allowing
inappropriate access to sensitive data and reports. Which of the following could have prevented this code
from being released into the production environment?
Question 134
While a threat intelligence analyst was researching an indicator of compromise on a search engine, the
web proxy generated an alert regarding the same indicator. The threat intelligence analyst states that
related sites were not visited but were searched for in a search engine. Which of the following MOST likely
happened in this situation?
Question 135
A penetration tester is preparing for an audit of critical that may impact the security of the environment. The includes the external perimeter and the intermitted of the environment. During which of the following processes is this type information normally gathered?