Question 91
In reviewing firewall logs, a security analyst has discovered the following IP address, which several
employees are using frequently:
152.100.57.18
The organization's servers use IP addresses in the 192.168.0.1/24 CIDR. Additionally, the analyst has
noticed that corporate data is being stored at this new location. A few of these employees are on the
management and executive management teams. The analyst has also discovered that there is no record
of this IP address or service in reviewing the known locations of managing system assets. Which of the
following is occurring in this scenario?
Question 92
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW. Which of the following types of information should be considered based on information traditionally found in the SOW? (Select two.)
Question 93
An organization is attempting to harden its web servers and reduce the information that might be disclosed by potential attackers. A security analyst is reviewing vulnerability scan results from a recent web server scan.
Portions of the scan results are shown below: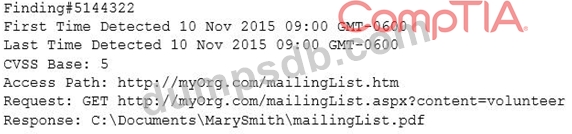
Question 94
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company's datacenter:
The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate.
Which of the following should the security administrator implement to harden the system?
Question 95
The director of software development is concerned with recent web application security incidents, including the successful breach of a back-end database server. The director would like to work with the security team to implement a standardized way to design, build, and test web applications and the services that support them.
Which of the following meets the criteria?

