Question 141
Following a data compromise, a cybersecurity analyst noticed the following executed query:
SELECT * from Users WHERE name = rick OR 1=1
Which of the following attacks occurred, and which of the following technical security controls would BEST reduce the risk of future impact from this attack? (Select TWO).
Question 142
A recent audit included a vulnerability scan that found critical patches released GO days prior were not applied to servers in the environment The infrastructure team was able to isolate the issue and determined it was due to a service disabled on the server running the automated patch management application Which of the following would Be the MOST efficient way to avoid similar audit findings in the future?
Question 143
A cybersecurity analyst is reviewing log data and sees the output below: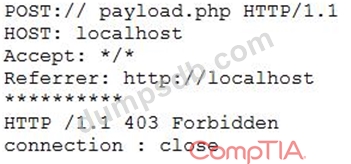
Which of the following technologies MOST likely generated this log?
Question 144
A security analyst's company uses RADIUS to support a remote sales staff of more than 700 people. The Chief Information Security Officer (CISO) asked to have IPSec using ESP and 3DES enabled to ensure the confidentiality of the communication as per RFC 3162. After the implementation was complete, many sales users reported latency issues and other performance issues when attempting to connect remotely. Which of the following is occurring?
Question 145
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW. Which of the following types of information should be considered based on information traditionally found in the SOW? (Select two.)

